Areas of emphasis manufacturers should review regarding CMMC
CMMC can have significant impacts on manufacturers, especially those in the defense industrial base or those working with the DoD.
Key points of the CMMC 2.0 update include:
- Simplified model: Reduced from 5 levels to 3 levels (Foundational, Advanced, Expert).
- Alignment with NIST SP 800-171: Level 2 (Advanced) aligns directly with NIST SP 800-171.
- Self-assessment option: Introduced for Level 1 and some Level 2 contractors.
- Elimination of CMMC-unique practices: Removed practices not included in other cybersecurity standards.
- Plan of Action and Milestones (POA&M): Allowed in certain situations for achieving certification.
- Waivers: Introduced a waiver process for certain CMMC requirements in limited situations.
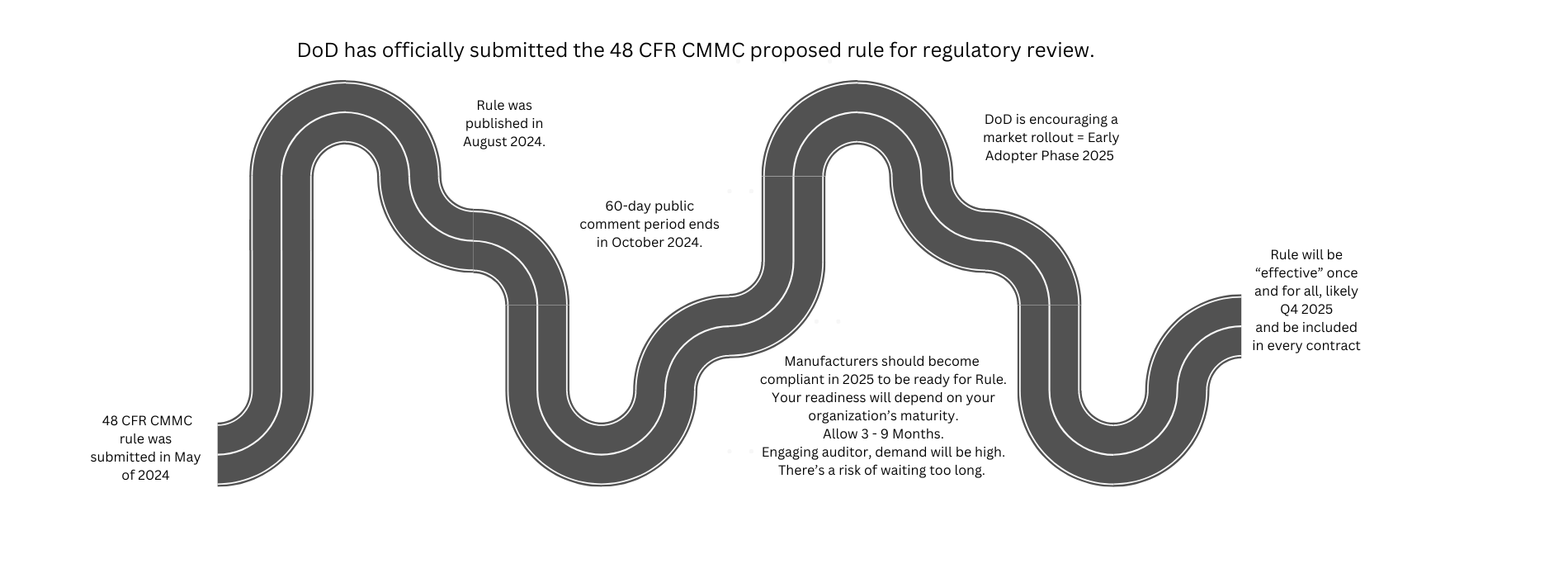
Prepare for 48 CRF CMMC Rule
Cybersecurity Standards
Manufacturers must meet specific cybersecurity standards based on their CMMC level. This may require implementing new security measures or upgrading existing ones.
- Compliance requirements: Manufacturers must meet specific cybersecurity standards based on their CMMC level. This may require implementing new security measures or upgrading existing ones.
- Cost implications: Achieving and maintaining CMMC compliance can involve substantial investments in technology, processes, and personnel. Smaller manufacturers may find these costs particularly challenging.
- Contract eligibility: CMMC certification is becoming a prerequisite for DoD contracts.Manufacturers without proper certification may lose access to certain business opportunities.
- Supply chain considerations: Manufacturers must ensure their suppliers also meet CMMC requirements. This can lead to changes in supplier relationships and procurement processes.
- Operational changes: Implementing CMMC may require adjustments to daily operations and workflows.This could include new procedures for data handling, access controls, and incident response.
- Cybersecurity Training and Awareness: Employees will need education on new cybersecurity practices and their importance. This may necessitate ongoing training programs and cultural shifts within the organization.
- Documentation and audits: CMMC requires thorough documentation of security practices and regular audits. Manufacturers must be prepared for increased scrutiny and record-keeping.
- Competitive advantage: Early adopters of CMMC may gain an edge over competitors in securing DoD contracts. CMMC compliance can also serve as a differentiator in non-defense markets.
- Technology infrastructure: Manufacturers may need to upgrade their IT systems to meet CMMC requirements. This could include new hardware, software, and network configurations.
- Risk management: CMMC implementation encourages a more proactive approach to cybersecurity. This can lead to better overall risk management and reduced vulnerability to cyber threats.
“How & why should my manufacturing organization proceed with NIST 800-171?”
Federal contract compliance:
-
- NIST 800-171 is mandatory for non-federal organizations that process, store, or transmit Controlled Unclassified Information (CUI) for federal agencies.
- Compliance is often a prerequisite for winning and maintaining government contracts.
Preparation for CMMC:
NIST 800-171 serves as a foundation for CMMC compliance, making the transition easier for manufacturers.
Scalable security framework:
The standard provides a scalable approach that can be adapted to various sizes of manufacturing operations.
Continuous Improvement:
Regular assessments required by NIST 800-171 promote a culture of continuous improvement in cybersecurity practices.
Office
7000 Stonewood Drive, Suite 222
Wexford, PA 15090
Hours
M-F: 8:30 am – 5 pm
Breach Hotline 24×7
Call Us
800-214-0957 (main)
800-214-0957 x700 (breach hotline)
