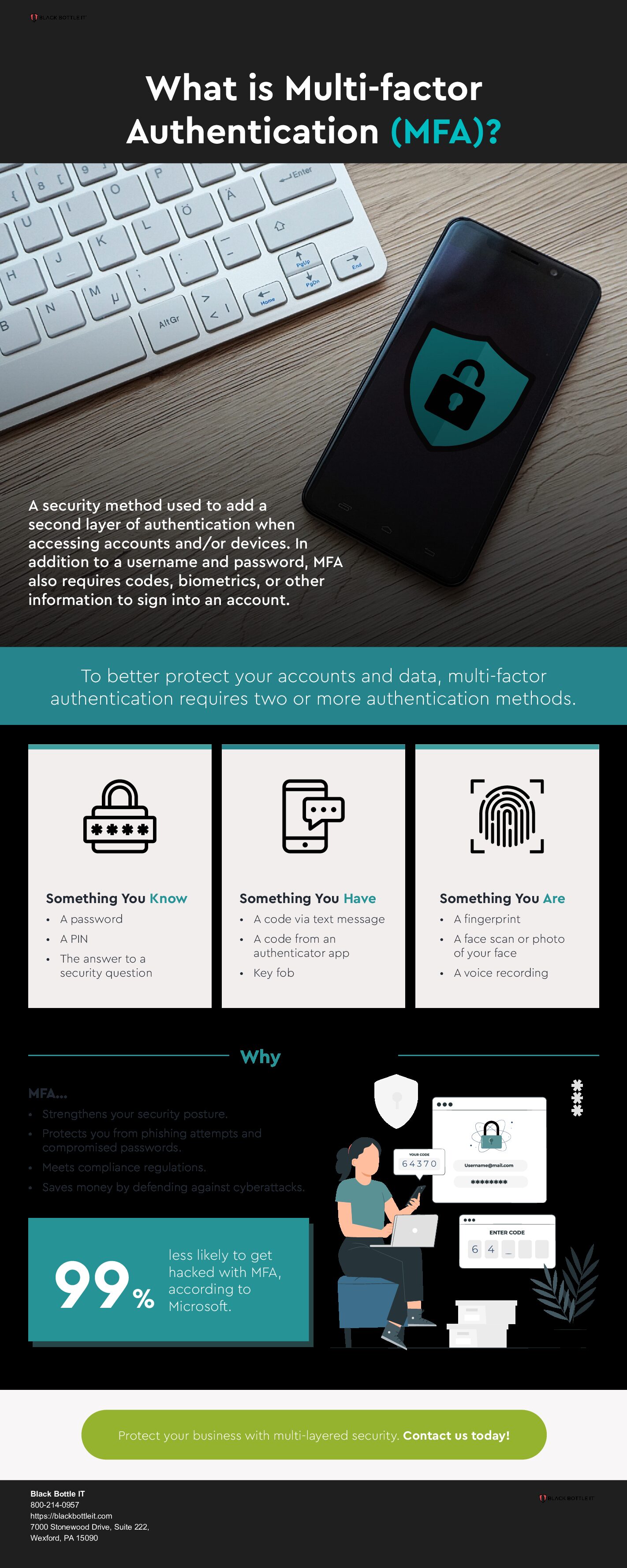
Data Data Everywhere. How Will You Protect Your Law Firm From Data Theft?
Cybersecurity is paramount for law firms due to the sensitive and confidential nature of the information they handle.
Law firms are among industries scrambling to keep up with an increasingly unsafe cyber landscape. The rate of global weekly cyberattacks rose by 7% in the first financial quarter of 2023 compared with the same period in 2022, according to an April report by cybersecurity firm Checkpoint Research.
Organizations faced an average of 1,248 attacks a week, Checkpoint found. One out of every 40 of the attacks targeted a law firm or insurance provider, the report said.
More than a quarter of law firms in a 2022 American Bar Association survey said they had experienced a data breach, up 2% from the previous year.
Here are several reasons why cybersecurity is crucial for law firms
Client Confidentiality: Law firms deal with highly confidential information, including client communications, legal strategies, and sensitive documents. A breach of this information could harm the firm’s reputation and lead to legal consequences.
Data Protection Compliance: Many jurisdictions have strict data protection laws that mandate organizations to protect the personal information of their clients and employees. Law firms must comply with these regulations, such as the General Data Protection Regulation (GDPR) in the European Union or the Health Insurance Portability and Accountability Act (HIPAA) in the United States.
Intellectual Property Protection: Law firms often handle intellectual property cases, and their intellectual property, such as legal precedents and strategies, is valuable. Remember, cybercriminals just want to get their hands on any sensitive information, and law firms must work with a third party who can monitor and protect against unauthorized access.
Financial Transactions: Law firms manage financial transactions for clients, which involves handling financial data. A breach could lead to financial loss, identity theft, or fraud.
Reputation Management: A cybersecurity breach can severely damage a law firm’s reputation. Clients trust law firms with their sensitive information, and a breach can erode that trust and lead to lost business.
Competitive Advantage: Law firms prioritizing cybersecurity are committed to protecting client interests. This can be a competitive advantage, attracting clients who prioritize security and confidentiality in their legal representation.
Ethical and Professional Responsibilities: Legal professionals are responsible for protecting client information. Failing to implement adequate cybersecurity measures could be seen as a violation of these responsibilities.
Operational Continuity: Cybersecurity is not just about preventing unauthorized access but also ensuring the availability and integrity of systems and data. A cyberattack can disrupt operations, and having robust cybersecurity measures in place helps ensure business continuity.
Client Trust and Confidence: Clients expect their law firms to handle their cases professionally and securely. Demonstrating a commitment to cybersecurity helps build and maintain client trust and confidence.
Legal Liability: In a cybersecurity breach, law firms may face legal consequences and liabilities. This could include lawsuits from clients whose information was compromised or regulatory fines for non-compliance with data protection laws.
The stakes are too high! Cybersecurity is essential for law firms to protect the confidentiality of client information, comply with data protection regulations, safeguard intellectual property, maintain their reputation, and fulfill ethical and professional responsibilities.
By budgeting, investing time and resources, and partnering with a Cybersecurity Consultant, you will sleep better at night as a business owner or partner.
Get started by understanding your gaps in cybersecurity.
Take our 5-minute Gap Cyber Risk Assessment Today!