Is Your Password Protection Duct Tape?
Yes, we are in the year 2025, and yet weak passwords remain one of the easiest entry points for cybercriminals. While your team focuses on growing the business, hackers systematically test common passwords like “123456” and “password123” against your systems.
The uncomfortable truth? Most businesses walk around with digital front doors held shut by nothing more than duct tape and good intentions.
If your employees still use their pet’s name plus their birth year, or worse, the same password across multiple accounts, you’re not just vulnerable—you’re practically inviting trouble.
But here’s the good news (and this has been no secret): robust password policies aren’t complicated to implement, and they’re one of the most cost-effective security measures you can deploy. The key is moving beyond the “just make it complicated” approach to a comprehensive strategy that actually works in the real world.
Let’s walk through exactly how to build password policies that protect your business without driving your team crazy.
Implementing strong password policies is crucial for protecting business systems. Here’s a more detailed breakdown:
Require complex passwords:
- Mandate a mix of uppercase and lowercase letters, numbers, and special characters
- Prohibit common words, phrases, or easily guessable information (like birthdates)
- Consider using passphrases instead of single words
- Set minimum length requirements (e.g., at least 12 characters)
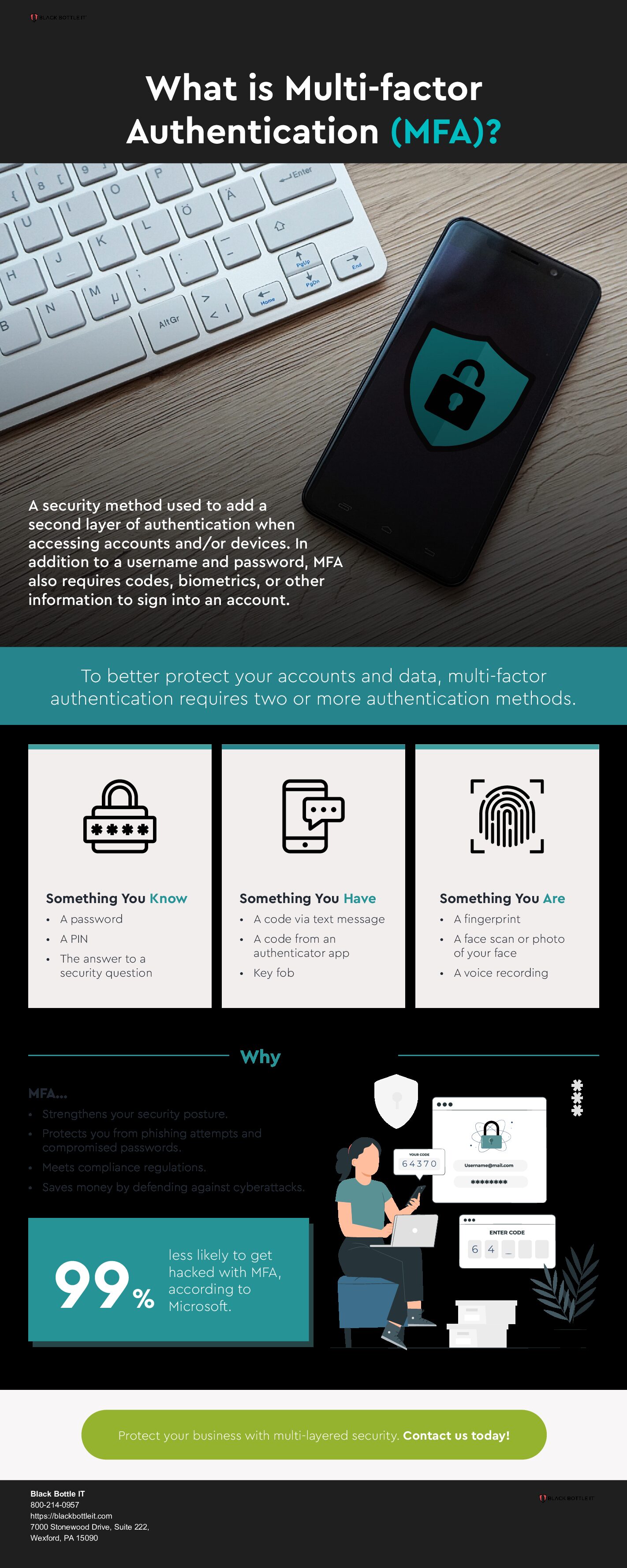
- A reminder to implement multi-factor authentication (MFA):
Require a second form of verification beyond passwords
Options include:
- Require a second form of verification beyond passwords
- SMS codes (though less secure than other methods)
- Authenticator apps (like Google Authenticator or Authy)
- Hardware tokens (such as YubiKeys)
- Biometric verification (fingerprints, facial recognition)
- Apply MFA to all critical systems and accounts, especially those with administrative access
Use password managers:
- Encourage or require employees to use reputable password management tools
- These tools generate and store strong, unique passwords for each account
- Reduces the risk of password reuse across multiple accounts
- Some options include LastPass, 1Password, or Bitwarden
Implement password rotation policies:
- Require password changes at regular intervals (e.g., every 90 days)
- Prevent the reuse of recent passwords
Monitor for compromised credentials:
- This is where Black Bottle IT comes in with services that check if employee email addresses or passwords have been exposed in known data breaches
- We will require immediate password changes if compromised credentials are detected
Implement account lockout policies:
- Our solution will lock accounts after a certain number of failed login attempts
- This helps prevent brute-force attacks
Use single sign-on (SSO) for multiple applications:
- Reduces the number of passwords employees need to remember
- Allows for centralized control and monitoring of access
By implementing these robust password policies, businesses can significantly reduce the risk of unauthorized access to their systems, making it much harder for hackers to intrude.
Contact Black Bottle IT today to remove the duct tape!