Where do Cyberattacks Start
Where do Cyber Attacks Start?
Cyberattacks can happen on any device at any given time, so how do you know which devices to protect your clients on? Well, to understand this, it will help to understand where these attacks come from.
In the past, all attacks came from outside sources, or, in other words, the internet. Cybersecurity companies combatted these attacks by setting up firewalls, IDS, and IPS systems to block any incoming attacks. Anti-virus software also became a reliable program to trust; however, these methods are outdated. Now, attacks can take place just about anywhere.
The malware that hackers now use is encrypted to the point that they are essentially invisible to firewalls and IDS systems. Historically, these edge devices acted as the first line of defense, protecting the network from outside threats, but this is no longer the case. The line of devices that attackers needed to penetrate before they could make a serious breach is no longer a concern to hackers.
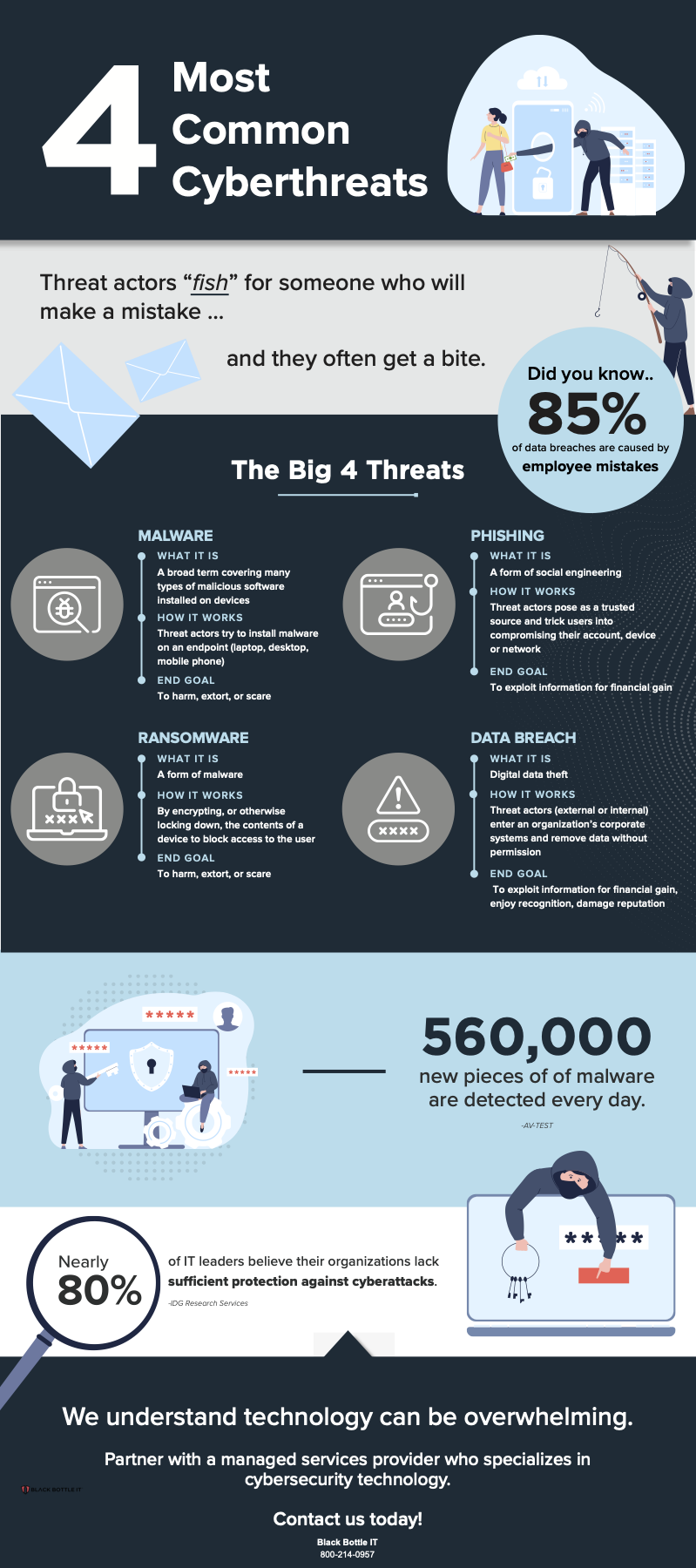
4 Most Common Cyberthreats!
Just as military tactics and weapons continue to advance, so do the methods of cyber threats. With these advancements, cyber attackers have devised multiple ways to bypass edge protection and gain direct access from inside the network. This is made possible through email phishing, accidentally entering an incorrect site, allowing your kids to play games on unsecured websites, and more.
Your Network is Vulnerable
While networks are still organized from edge devices to wireless access points, and then to servers and personal devices, these advanced malware attacks ignore the line of defense that once proved competent. Companies do not realize that attacks can take place from within their network. In fact, many companies still rely on firewalls and anti-virus software. This is not enough. Rather than simple edge protection, companies need cybersecurity solutions that give them full coverage.
With solutions from a reliable cybersecurity company, when an attack is made — no matter where it is coming from — the company is notified immediately, and the attack can be isolated before it spreads. This combination gives companies a centralized security system with all the necessary assistance.