Lessons From the Breach Hotline
Email Compromise Trends The Highest on Breach Hotline: Lessons Learned
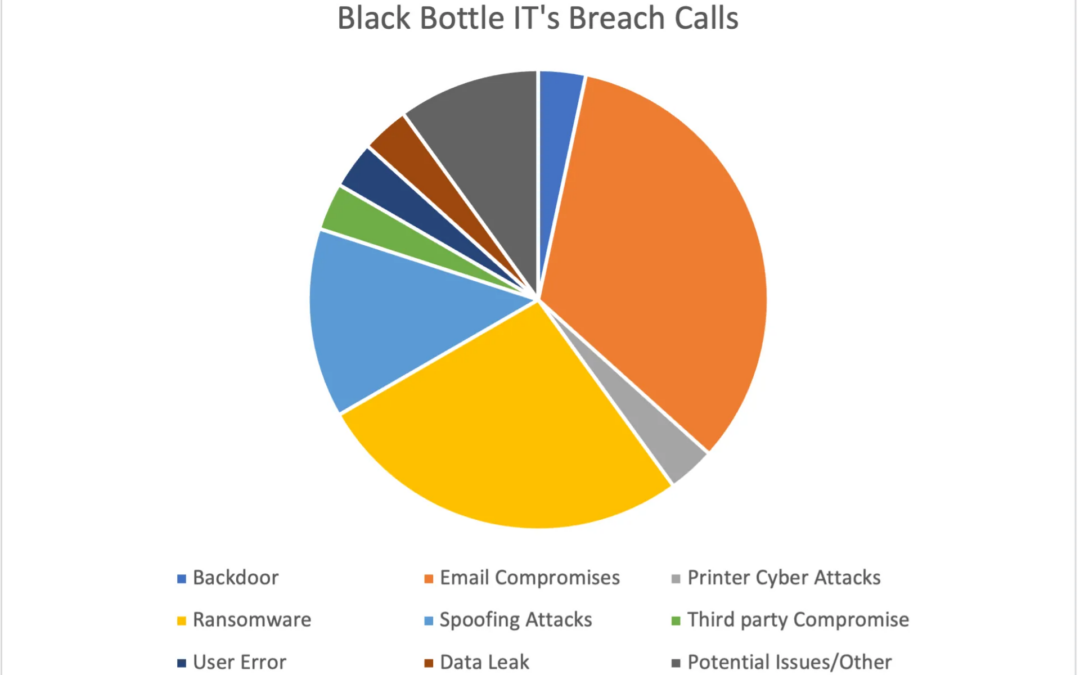
Breaches happen to ALL businesses. Of the calls into the Black Bottle IT Breach Hotline, 33% directly resulted from email compromise and user error! Unsurprisingly, ransomware was a close second that resulted in calls to the Breach Hotline.
Most often, scammers go right for the finance employees and their emails, and they use phishing or malware to access a finance employee’s email account, such as an accounts receivable manager. Then the scammer emails the company’s suppliers fake invoices that request payment to a fraudulent bank account.
Types of Breaches You Should Know About
- Backdoor Attack: A backdoor is a malware type that negates standard authentication procedures to access a system. As a result, remote access is granted to resources within an application, such as databases and file servers, allowing perpetrators to issue system commands and update malware remotely.
- Printer Cyber Attacks: Hackers can connect your printer to a botnet, which can be used to steal your data and carry out cyber attacks.
- Spoofing Attacks: When someone or something pretends to be something else in an attempt to gain your confidence, get access to your systems, steal data, steal money, or spread malware.
- User Error: An unintentional or lack of action results in a data breach; this category includes activities like downloading infected software and keeping a weak password.
- Email Account Compromise: EAC is not limited to phishing and malware emails to compromise victims’ email accounts, gaining access to legitimate mailboxes.
- Ransomware: During the first half of 2022, there were an astonishing 236.1 million ransomware attacks worldwide. The top five industries impacted include Banking and Financial Services, Education, Energy and Utilities, Government, and Manufacturing.
- Third-Party Compromise: Third-party risk is the likelihood that your organization will experience an adverse event: data breach, operational disruption, or reputational damage. A third-party attack occurs when a criminal infiltrates your system through an outside partner or provider with access to your systems and data.
- Data Leak: A data leak is when sensitive data is accidentally exposed physically, on the Internet, or any other form, including lost hard drives or laptops. This means a cybercriminal can gain unauthorized access to sensitive data without effort. The consequences may include the destruction or corruption of databases, the leaking of confidential information, and the theft of intellectual property.
What Can Businesses Do to Protect Themselves
According to Michael Valentine, Black Bottle IT’s Compliance Security Expert, the businesses that called their breach hotline over the last 24 months did not have monitoring; some only had Anti-Virus or nothing at all.
Having an incident response plan to manage third parties is also a must. While the benefit typically outweighs the risk for many third-party relationships, partnering with third parties increases your attack surface risk. At Black Bottle IT, we answer third-party relationships as it is not necessarily “if” but when an incident will occur and how severe it will be.
Human error continues to be a concern. Black Bottle IT and industry experts agree that Cybersecurity training should occur about two to three times per year — or almost every four to six months. One of the most common reasons security training programs fail is a lack of adequate planning and effort on behalf of organizations.




