Blog
Most Popular Posts
Cybersecurity for Managing Partners
Cybersecurity for Managing Partners: Your Fiduciary Duty to Protect...
Payroll Companies are a Lucrative Business for Hackers
Payroll Companies are a lucrative business for hackers. We will help your organization meet compliance and become cyber-resilient.
The Remote Work Security Gap
The Remote Work Security Gap No One's Talking About Real Talk: Your...
Cybersecurity Awareness Training: Not an Annual Checkbox
Cybersecurity awareness training shouldn't be treated as an annual...
Deepfake Fraud: The $40 Billion Threat Targeting Small Businesses
By John Hensberger, Founder, Black Bottle IT Small business owners, we...
Is Your Password Protection Duct Tape?
Black Bottle IT Cybersecurity Consultants are crucial in assisting businesses with SOC 2 compliance by providing expertise and guidance.
SOC2 Certification: A Critical Investment
In today's digital financial landscape, data security and privacy have...
Preparing for AI
Black Bottle IT is Joining the PASBA Spring Summit in Clearwater,...
We’re Joining the IPPA Spring Summit
Join Black Bottle IT at IPPA Spring Summit in Vegas! We're packing our...
Digital Spring Cleaning: A Must for PCI Compliance
If you process even a single credit card transaction, this message is for...
Beyond Break-Fix: Transform Your IT with Proactive Management
Implementing a comprehensive, proactive maintenance strategy through...
Make it Harder for Hackers to Intrude
Implementing strong password policies is crucial for protecting business...
Going Beyond Boundaries. The Need to Define Access Controls
Access controls ensure that only authorized users have access to sensitive information. Contact Black Bottle IT to get started today.
The More Cybersecurity Changes The More it Remains the Same
“The more things change, the more they stay the same” means that despite apparent changes or advancements, certain fundamental aspects or patterns remain unchanged over time. One could relate this to cybersecurity. Continue Reading.
Data Data Everywhere. How Will You Protect Your Law Firm From Data Theft?
The stakes are too high! By budgeting, investing time and resources, and partnering with a Cybersecurity Consultant, you will protect your law firm from data theft.
The Difference Between Passwords, Fingerprint, MFA
MFA: strengthens your security posture, protects you from phishing attempts and compromised passwords, and meets compliance regulations. Continue reading:
Where do Cyberattacks Start
With solutions from a reliable cybersecurity company, when an attack is made — no matter where it is coming from — the company is notified immediately, and the attack can be isolated before it begins to spread. Continue reading…
What Managed IT Solution is Best for Your Business?
There is always a go-forward managed it cybersecurity plan that is right for you, your business, and your stakeholders.
Embrace Cybersecurity with Your Partners and Vendors
As cybercrime is always knocking on the door of your business, one of the most crucial things you can do is partner with vendors that embrace a good cybersecurity posture.
Black Bottle IT Achieves HIPAA Compliance with Compliancy Group
Black Bottle IT Achieves HIPAA Compliance with Compliancy Group by completing its proprietary HIPAA compliance process.
Cybersecurity, in General, Doesn’t Have to Be Hard.
Black Bottle IT simply recommends protecting your business without a big pot of gold. Our affordable solution gets you to Cybersecurity Secured!
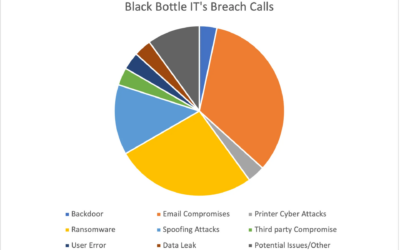
Lessons From the Breach Hotline
Our Breach Hotline takes calls from businesses of all shapes and sizes when they suspect they’ve had a cyber security incident.
Black Bottle IT Joins MSP Alliance®
Black Bottle IT joins MSP Alliance’s vibrant global consortium of cloud managed service providers, and technology-enabling vendors.
What Does Cybercrime Look Like
Business owners seek a complete Risk Management Solution and Black Bottle IT understands the ever-changing landscape. Continue reading to learn more:
Office
7000 Stonewood Drive, Suite 222
Wexford, PA 15090
Hours
M-F: 8:30 am – 5 pm
Breach Hotline 24×7
Call Us
800-214-0957 (main)
800-214-0957 x700 (breach hotline)